.png)
Ditch the frankensteined stack of security tools, for a single place to find and fix vulnerabilities across your code, cloud, and infrastructure.
.avif)
See which issues matter most, based on real risk and your environment.
Tune prioritization to how your tech stack actually works.
One-click fixes for common issues, or agent-driven PRs for code changes.
.png)
.avif)
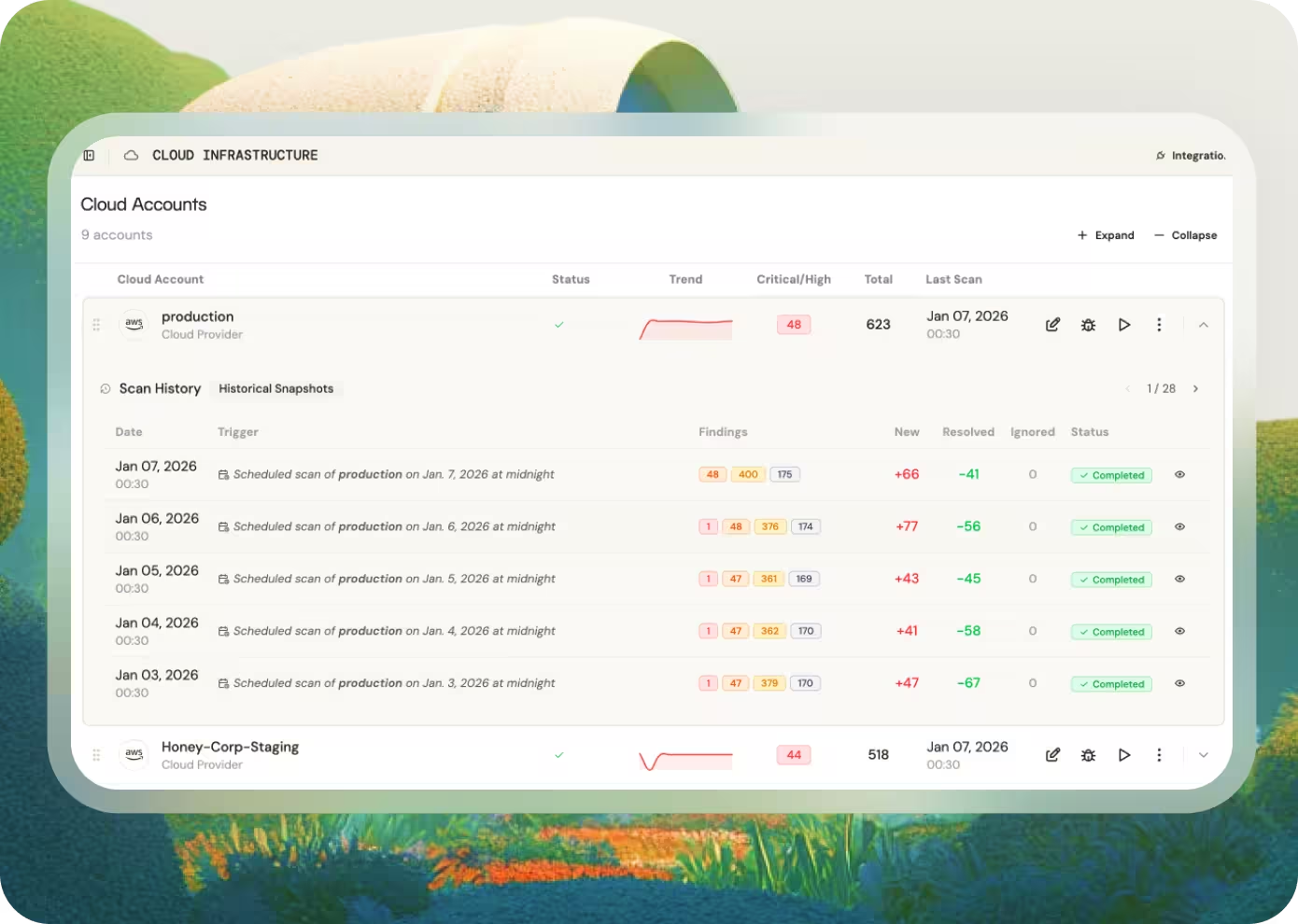
Continuous visibility into infrastructure, devices, repositories, services, and dependencies, without spreadsheets or one-off scans
Auto-generate a detailed inventory of software components in CycloneDX or SPDX formats
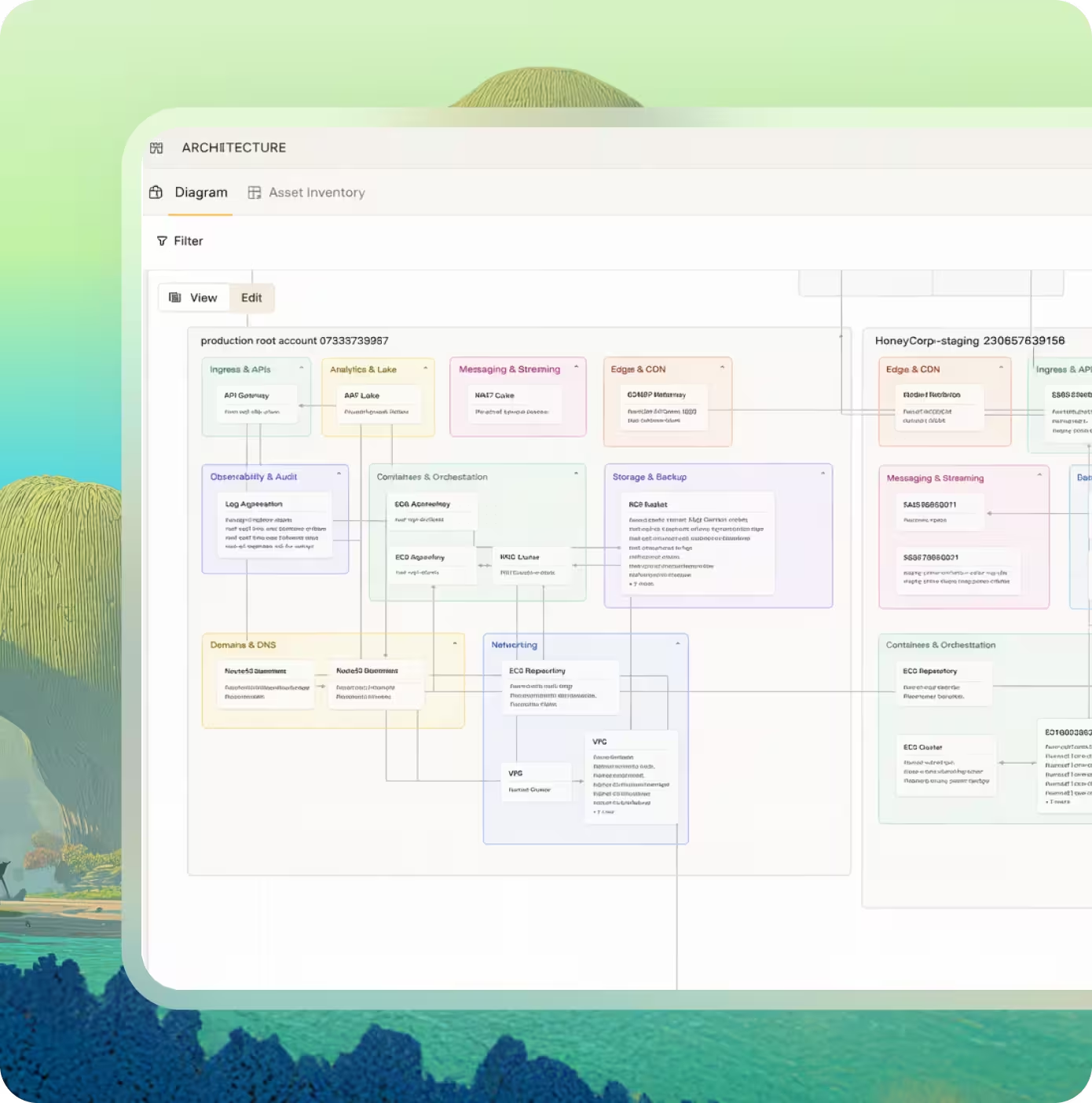
Auto-generate a current view of system & network architecture, make edits, and export to other tools for deeper customization
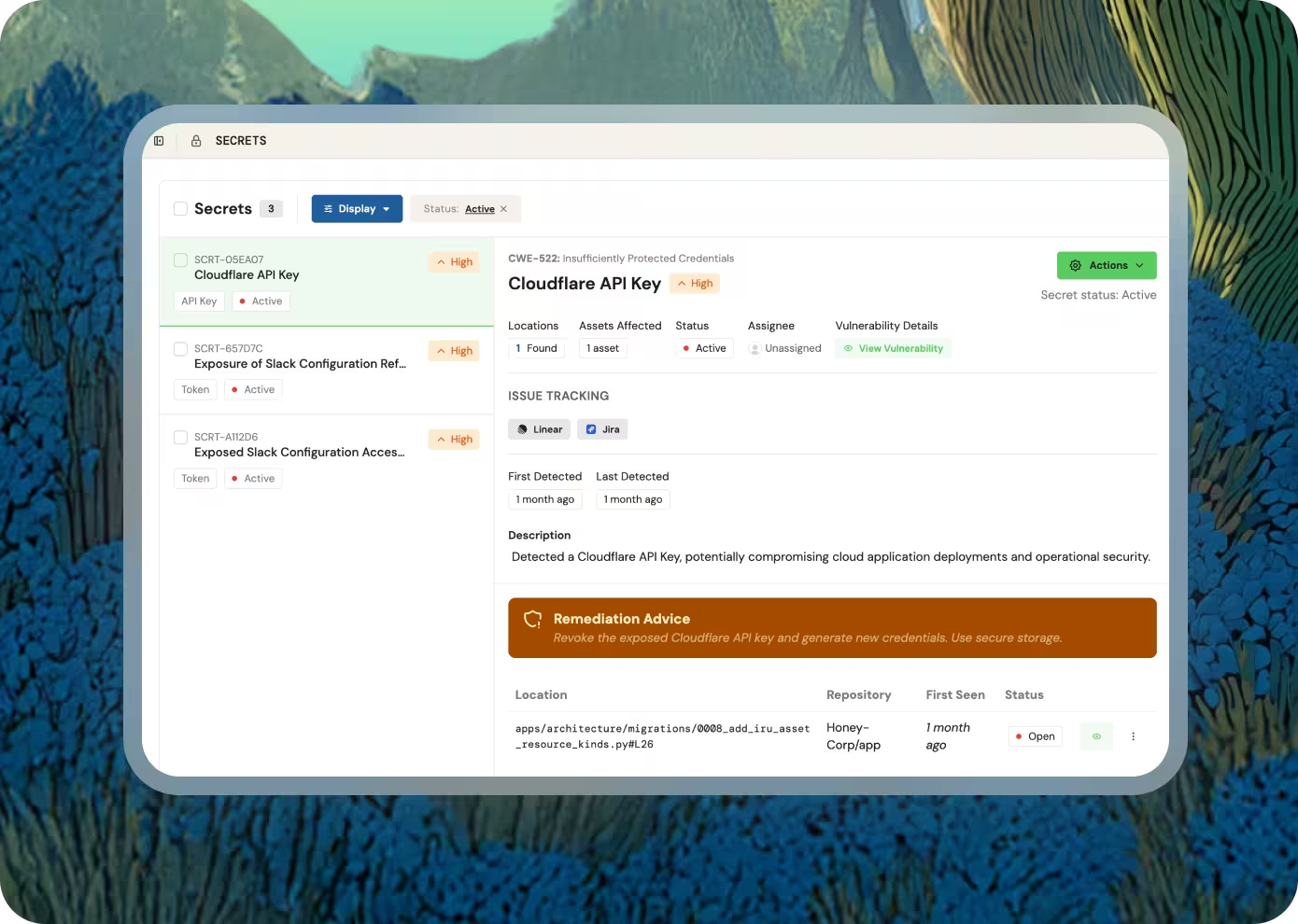
Findings, evidence, and ownership in one place.
Know what’s fixed, what’s open, and what’s left.
Provide evidence for audits, customers, and diligence.
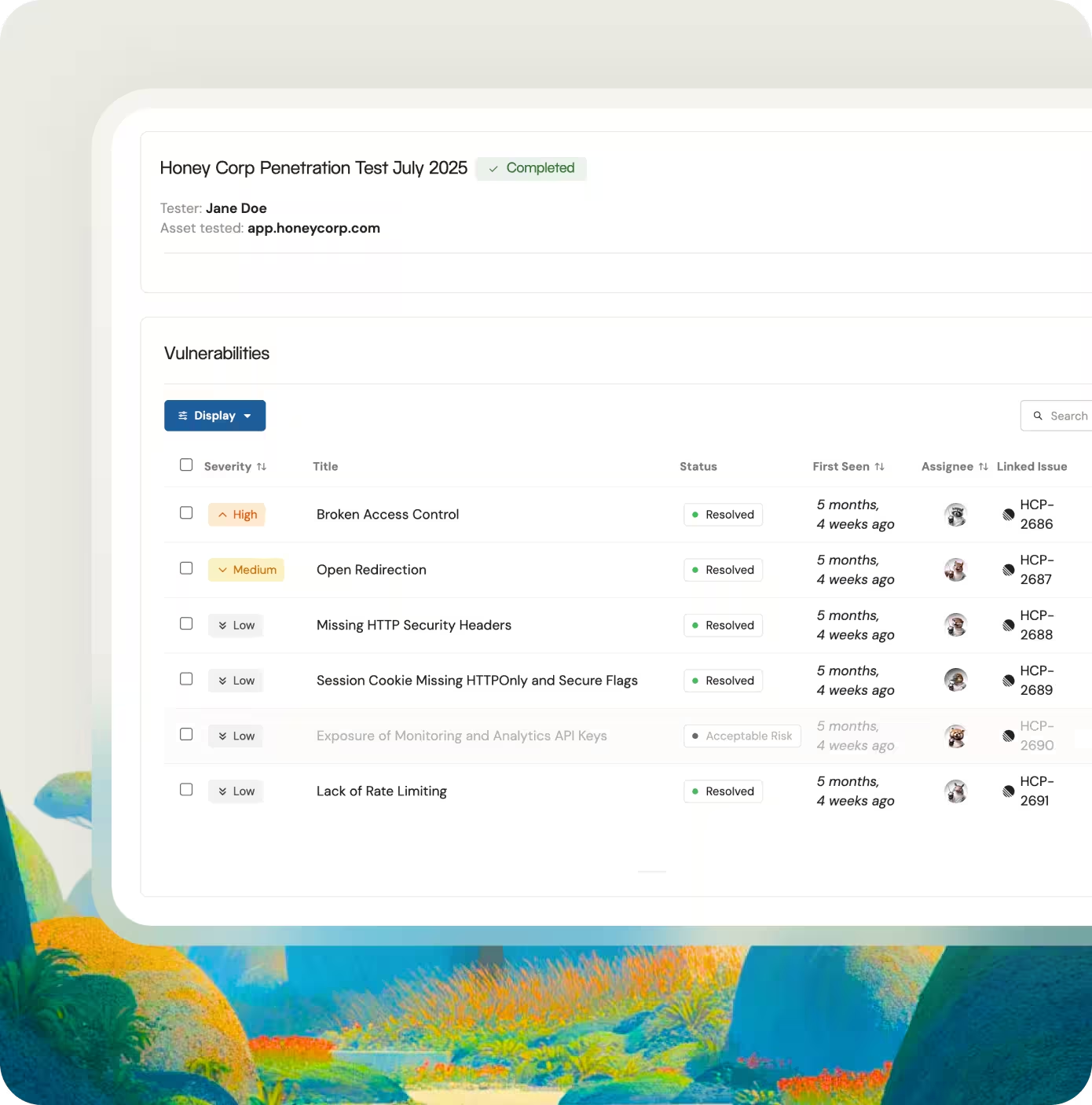

— Ben Papillon
CTO & Co-founder, Schematic